If you are currently using version 5.x.x, we advise you to upgrade to the latest version before the EOL date. You can find the latest documentation here.
Geneos on Amazon Web Services Cloud
Overview
This guide provides you the list of considerations and recommendations when deploying Geneos on Amazon Web Services (AWS). In addition, this guide defines the requirements needed to deploy Geneos on Amazon Elastic Compute Cloud (EC2).
The illustration below shows a running Geneos environment with Gateway and Netprobe components that are connected to AWS:
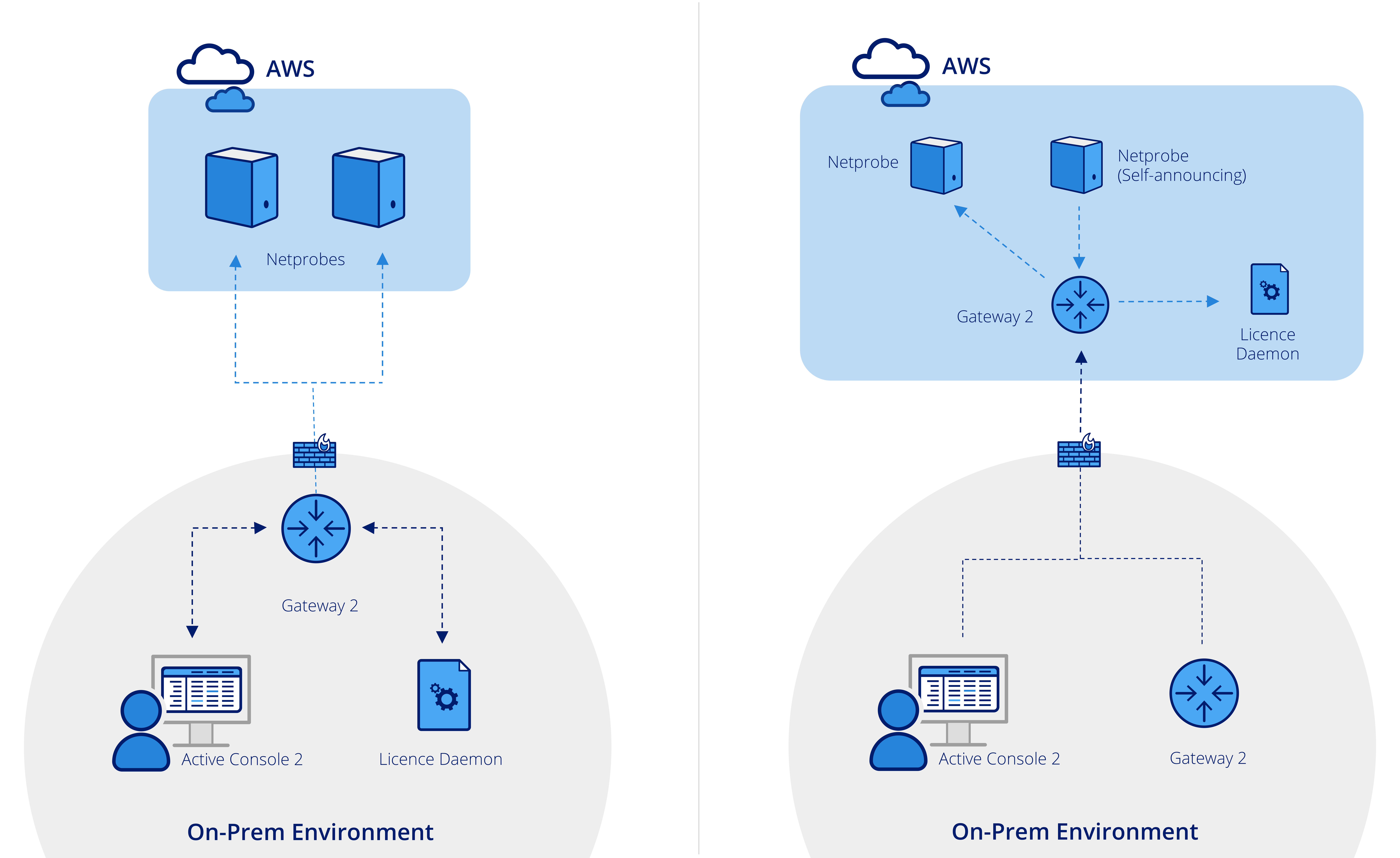
- Active Console running on-premises that connects to Gateway on EC2 instance.
- Netprobes and Self-Announcing Netprobe) on EC2 instance that connects to Gateway running on-premises.
Prerequisites
Having a basic understanding of how to download, run, and configure a Netprobe and Gateway is required before you can proceed. For how to configure and install these components, refer to the following guides:
- Netprobe quickstart guides
- Gateway Installation Guide
The following requirements for both Geneos and Amazon Web Services environments must be met prior to the setup of this deployment.
Geneos connection requirements
This section provides the requirements for connecting one Geneos component to another when deploying to AWS. EC2 instances may not be able to access machines in an internal network, unless those machines are set up with a public IP address.
- Active Console must be able to connect to Gateways.
- Gateways must be able to connect to Licence Daemon. See Connect to the Licence Daemon in Gateway Licensing.
- Gateways must be able to connect to Netprobes (normal Netprobe mode).
- Self-Announcing Netprobes must be able to connect to Gateways (in Self-Announcing Netprobe mode).
- Importing Gateways must be able to connect to exporting Gateways.
- Floating Netprobes must be able to connect to Gateways
Amazon Web Services EC2 system requirements
The system requirements for Amazon Elastic Compute Cloud (EC2) are available on their website. Ensure that the EC2 instances have instance types that meet the machine requirements for Gateway and Netprobe.
To check the system requirements for Gateway and Netprobe, refer to the following guides:
- Gateway System Requirements in Gateway Installation Guide
- Netprobe system requirements
The EC2 Security Groups, as well as the corresponding subnets, routing tables, internet gateways, should allow access to the ports. Below are some recommendations:
- For relatively short-lived instances, use Self-Announcing Netprobes.
- Deploy Gateways and Licence Daemons on the same virtual private cloud or VPC (different subnets can be used, as long as the subnet configurations allow for the connectivity).
Performance and cost considerations
Be aware that the amount of traffic between AWS and an internal network has an implication on the cost . The following are instances which involve high traffic:
- Active Console instances in an internal network connecting to Gateways in AWS. The recommendation is not to leave the Gateway connections from the Active Console open when not needed. If a virtual private cloud (VPC) is hosting several Gateways, it is recommended to create a single importing Gateway which can handle connections to an internal network.
- Gateways on AWS exporting to Gateways in an internal network. The recommendation is only to export the necessary entities (and aggregate dataviews, if possible).
-
Gateways in an internal network connecting to Netprobes on AWS. Multiple Netprobes with fairly regular sampling periods could mean a lot of network traffic. If possible, place the Gateways on AWS to minimize this traffic.
Example setup and dataviews
The following procedures list how to set up your AWS instance and the configurations required to connect to Geneos components.
- Connect to the EC2 instance through SSH
- Download the Gateway and Netprobe packages
- Set up Gateway Setup Editor
Connect to the EC2 instance through SSH
Note: Ensure that your EC2 instance is running and that you already obtained the license key and host IP address. To know more about EC2 instances, visit the Amazon Web Services website.
To configure your AWS instance, follow these steps:
- Download an application that allows you to transfer files to your AWS instance.
- Connect using the remote host and username of your running AWS instance.
- Provide the private key that is used to generate the EC2 instance.
- Click OK.
In this example, MobaXterm is used to connect through a Secure Shell (SSH).
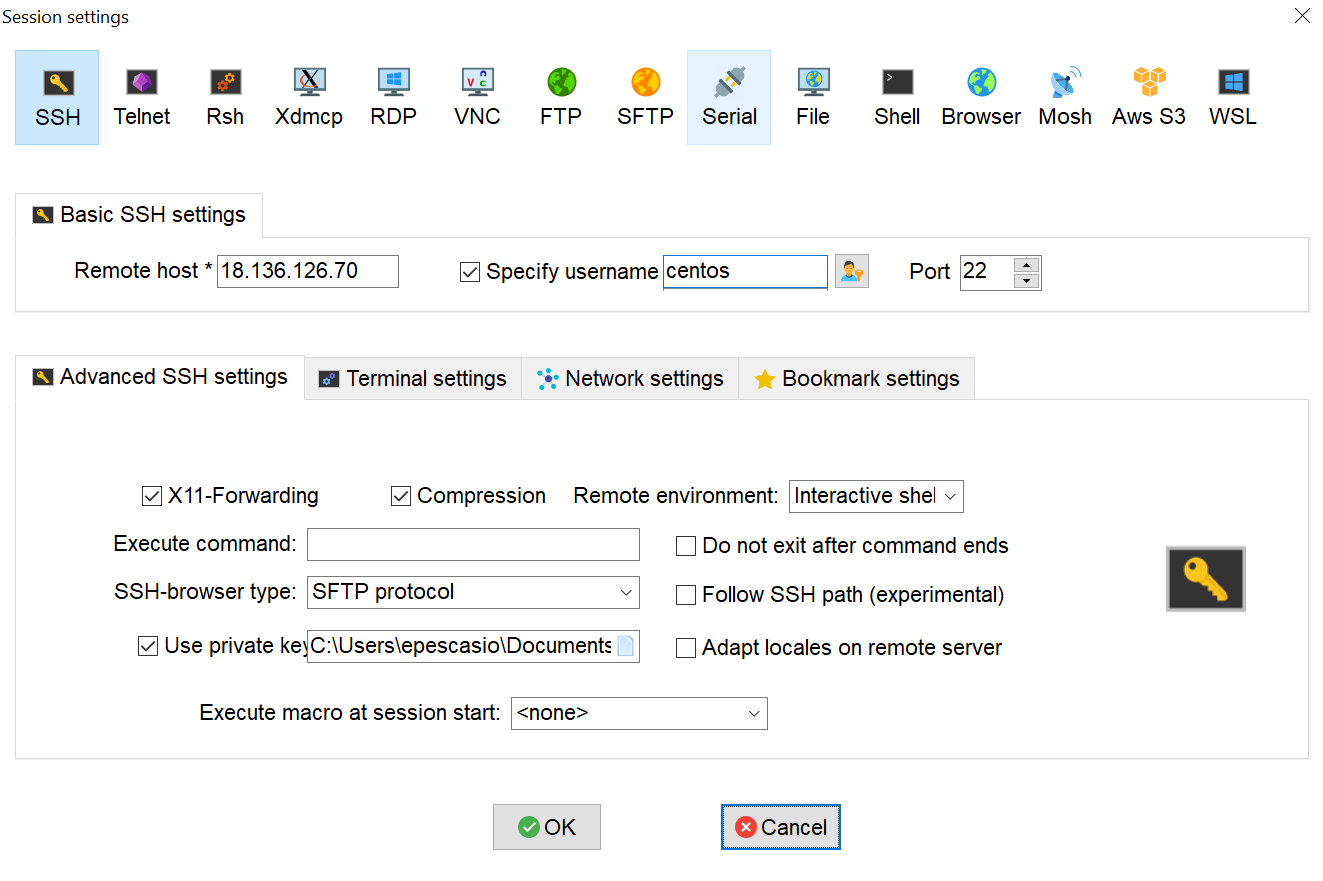
Provide these information in the Session settings screen:
| Field | Description |
|---|---|
| Remote host | Hostname or IP address of the EC2 running instance you created in Amazon Web Services. |
| Specify username | centos or depending on the AMI you used to generate EC2 instance. |
| Port | Default value: 22 |
| Private Key | Path to the downloadable file received when you generated the EC2 instance in Amazon Web Services. |
This shows the fields during the configuration of your session settings:
Note: There are other applications that you can use to connect through a Secure Shell (SSH).
Download the Gateway and Netprobe packages
The procedures on how to download these Geneos components are available to their corresponding documentation guides. Open the following resources:
- To download Gateway, see How to download and unpack Gateway in Gateway Installation Guide.
- To download Netprobe, see the Netprobe quickstart guides in the Netprobe Documentation Home.
Once these files are saved on your local machine, follow these steps:
- Connect to your EC2 instance using SSH.
- Copy the Gateway binaries to your EC2 instance.
- Copy the Netprobe binaries to your EC2 instance.
In summary, this section only asks you to migrate the binaries of Gateway and Netprobe into the EC2 instance.
Set up Gateway Setup Editor
Note: As part of the Geneos connection requirements, ensure that your Gateway and Netprobe are up and running properly.
To connect Gateway to the Netprobe on EC2 instance, follow these steps:
- Open Active Console.
- Connect to the Gateway that is running on the EC2 instance.
- Create a probe in Gateway Setup Editor.
- Provide a name and hostname.
- Add a defined probe to a managed entity.
- Create a sampler which depends on what you wish to monitor or use.
- Click Save to apply your changes.
Provide the following information in the Probes section in Gateway Setup Editor:
| Field | Description |
|---|---|
| Name | Name of the probe. |
| Hostname | Hostname or IP address of the EC2 running instance you created in Amazon Web Services. |
| Port | Default value: 7036 |
This dataview in Active Console monitors the CPU sampler of the AWS instance: