Connect to SSO provider
SSO authentication Copied
To use SSO, the Geneos administrator needs to enable SSO logins for each Gateway and to ensure either that Obcerv or Gateway Hub is configured to provide identity management services to Geneos or that at least one instance of the Geneos SSO Agent is running.
Configure Active Console for SSO Copied
To use SSO login authentication in Active Console
- Open Active Console on the operating system platform on your machine.
- Go to Workspace > General settings. See Workspace settings.
- Enter the agent’s URL in the SSO Agent URL field.
- For Obcerv, the URL includes the Obcerv realm name. For example:
https://obcerv.example.com/auth/realms/obcerv - For SSO Agent or Gateway Hub, the URL includes only the protocol, hostname, and port. For example:
http://sso-agent.dev:8088
- Click Save to apply the changes.
- Click SSO Login on the toolbar.
Set up one or more Gateway connections to use the SSO Logon method, either individually or through the workspace logon setting. For more information, see Gateways Dockable and Workspace settings.
Note
Versions of Active Console before version 4.3 cannot process a configuration that references an unknown login method. If these encounter references to the SSO logon method, these fail to load any connection details at all. If your workspace file specifies SSO as the workspace logon type or if it specifies SSO as the logon method for any connection, you cannot use it with an older version of Active Console. Additionally, a remote connection file which specifiesLM_SSOas the logon method for any connection cannot be used with an older version of Active Console.
The Active Console supports SSO Agent connections with Kerberos, and negotiates authentication on macOS and Ubuntu. For more information, see SSO Agent User Guide.
If an error occurs when connecting to SSO Agent in the Active Console on macOS or Ubuntu:
- Check that the values in the
krb5.conffile are valid. This is located in the installation folder/resources/configurationof your application. - Open Active Console and follow the same steps when connecting to SSO Agent.
This is an example configuration of krb5.conf file:
[libdefaults]
default_realm = <user-domain>
default_tkt_enctypes = aes128-cts rc4-hmac des3-cbc-sha1
des-cbc-md5 des-cbc-crc
default_tgs_enctypes = aes128-cts rc4-hmac des3-cbc-sha1
des-cbc-md5 des-cbc-crc
permitted_enctypes = aes128-cts rc4-hmac des3-cbc-sha1
des-cbc-md5 des-cbc-crc
[realms]
<user-domain> = {
kdc = <active directory IP addres, example 192.168.10.2>
default_domain = <user-domain>
}
[domain_realm]
.<user-domain>= <user-domain>
Use the SSO login and logout button Copied
If your Active Console is in the same NT domain as the SSO Agent, Active Console logs you in automatically, assuming that one or more Gateways are available and set up to use the SSO login method.
The SSO Login/Logout button, which appears in the toolbar area of the ActiveConsole 2, allows you to log in and out manually:
- If you are logged in through SSO, the button is labelled SSO Logout. Clicking it logs you out and any SSO Gateways are displayed in grey, as if these are disabled.
- If you are not logged in, the button is labelled SSO Login. Clicking it logs you in and establish connections to any SSO Gateways, other than those which have been explicitly disabled through the Connections settings dialog or by using the “Disconnect” menu action.
- If the SSO Agent URL has not been configured, the button is disabled.
Connect to Obcerv using a web browser Copied
Beginning 6.7.x, there are now two options available for connecting to Obcerv, either through the default username and login dialog or via a web browser through Open ID Connect or OIDC.

- Direct – If this is selected, SSO agent URL login is done via a username/password dialog. By default, this setting is selected.
- OIDC – If this is selected, SSO agent URL login is done by opening a web browser.
If OIDC is selected, there are two scenarios may prompt Obcerv or the OIDC server to load in the web browser:
- By clicking the SSO Login button
- Connecting to a Gateway that uses the SSO logon method

In the Active Console, the SSO Login button will be changed to Pending. If you click on the Pending button, you will be given the choice to cancel the SSO login process.
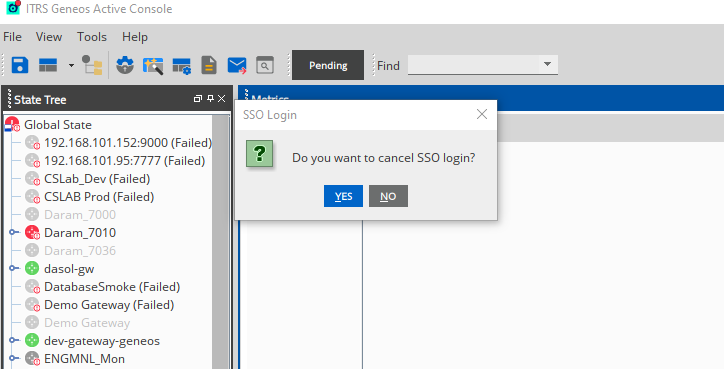
Upon successful login to Obcerv (or the OIDC) in the web browser, you will be redirected to a web page from the Active Console confirming the successful login, and you can now proceed to use the Active Console. At this point, the Active Console is connected, and the SSO Login or Pending button is changed to SSO Logout.
To ensure accessibility of the Active Console’s redirect page by Obcerv, it is necessary to include http://localhost/* in the Valid Redirect URIs configuration of the geneos-ui client in Obcerv.
Additionally, Active Console uses Proof Key for Code Exchange (PKCE) when the SSO agent URL is Obcerv or any Keycloak instance, and the SSO connection type is OIDC. PKCE is used when attempting to login to Obcerv via a web browser.
Web Dashboard uses PKCE when SSO authentication is configured, and the SSO agent URL is Obcerv or any Keycloak instance. PKCE is used when attempting to login to Obcerv via a browser.
PKCE is configured in the Realm section of Obcerv → obcerv → Clients → geneos-ui → Advanced → Proof Key for Code Exchange Code Challenge Method.
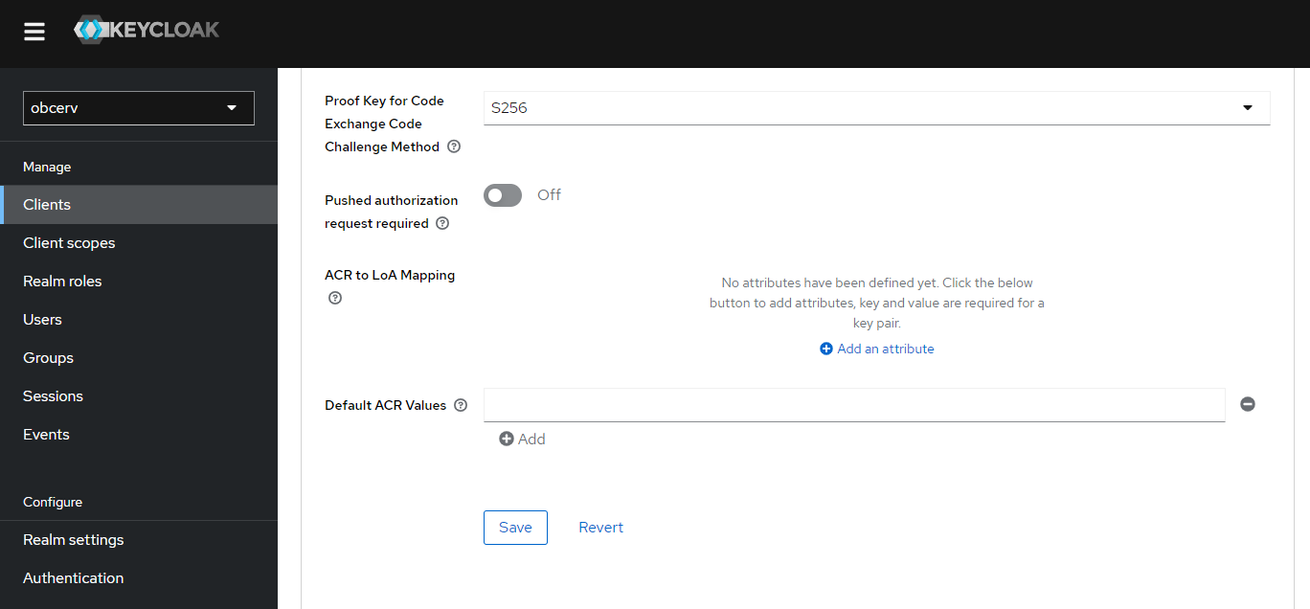
PKCE offers three choices: None, S256, and Plain. Both Active Console and Web Dashboard are compatible with S256. Provided that Obcerv or Keycloak’s PKCE is set to either None or S256, login attempts by Active Console and Web Dashboard will be successful. However, it is important to note that they do not support the Plain PKCE format.