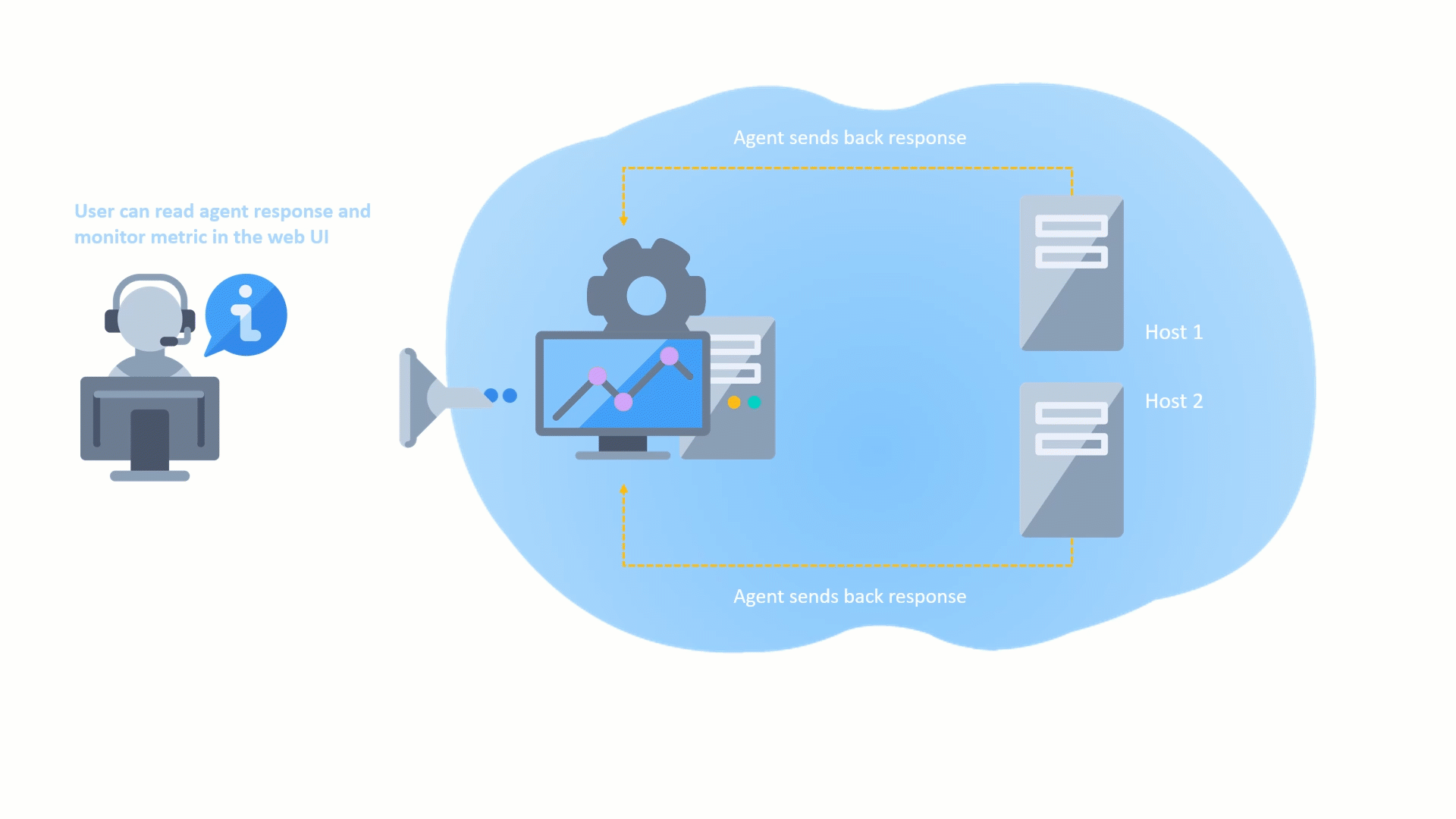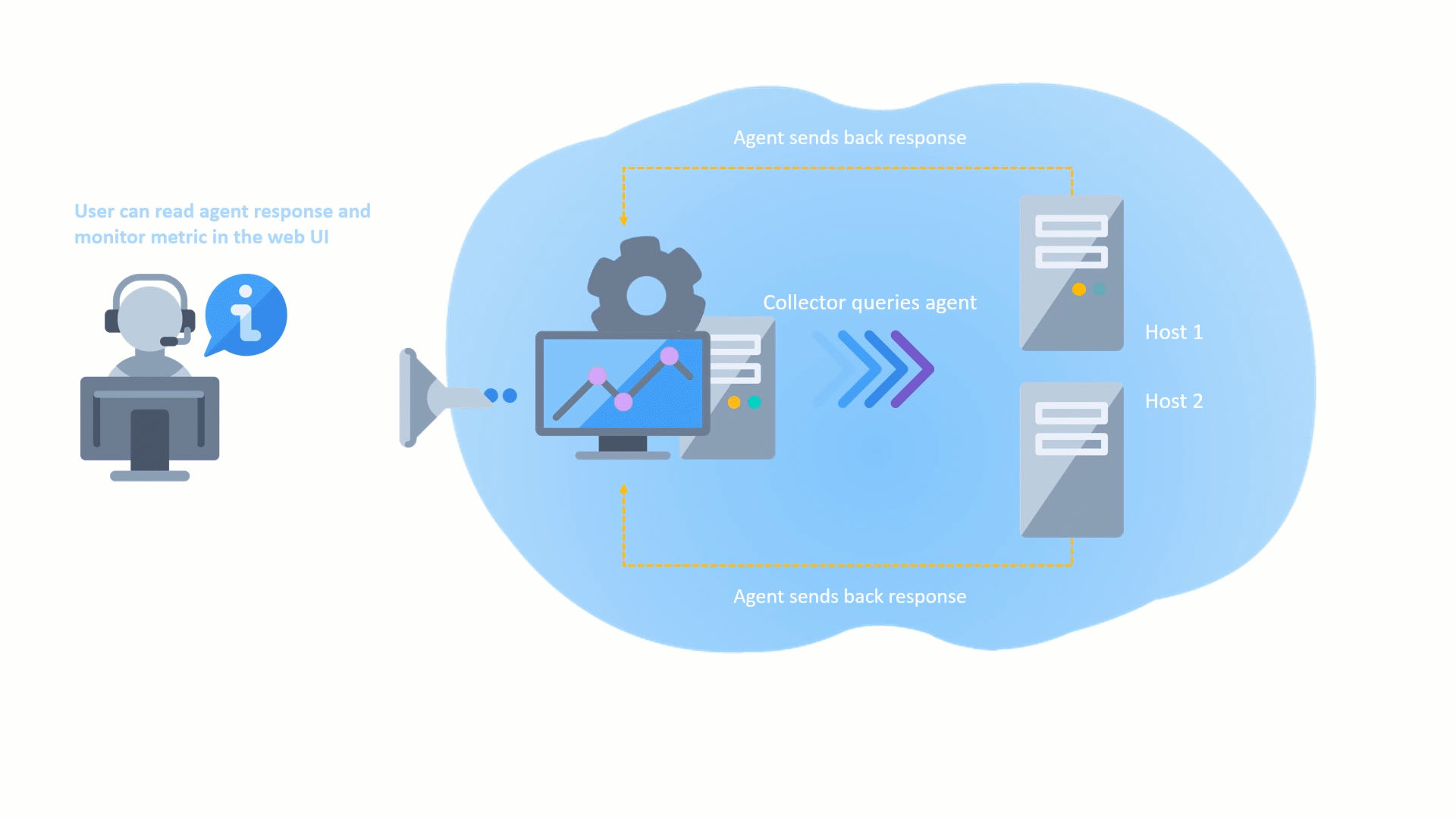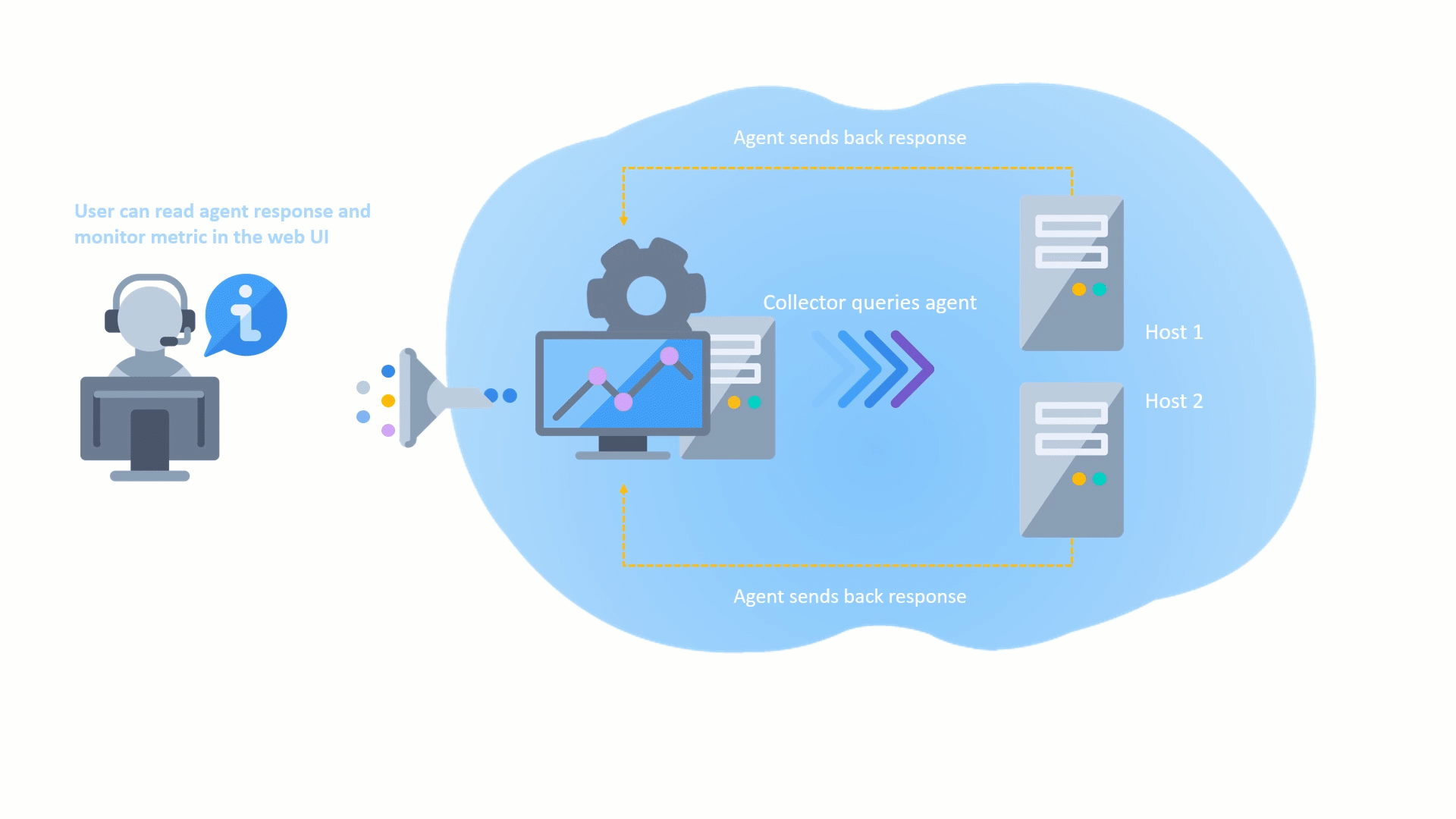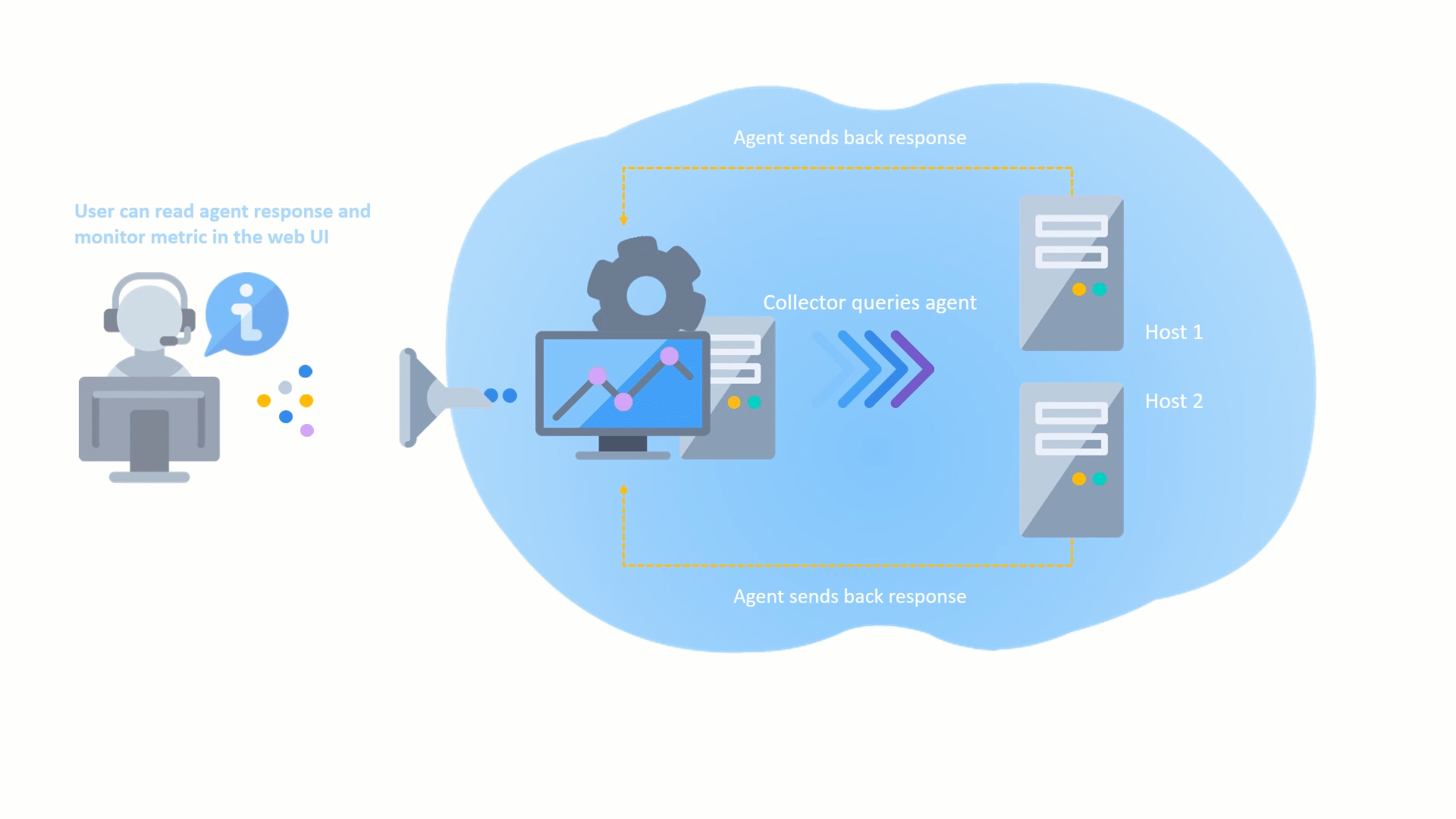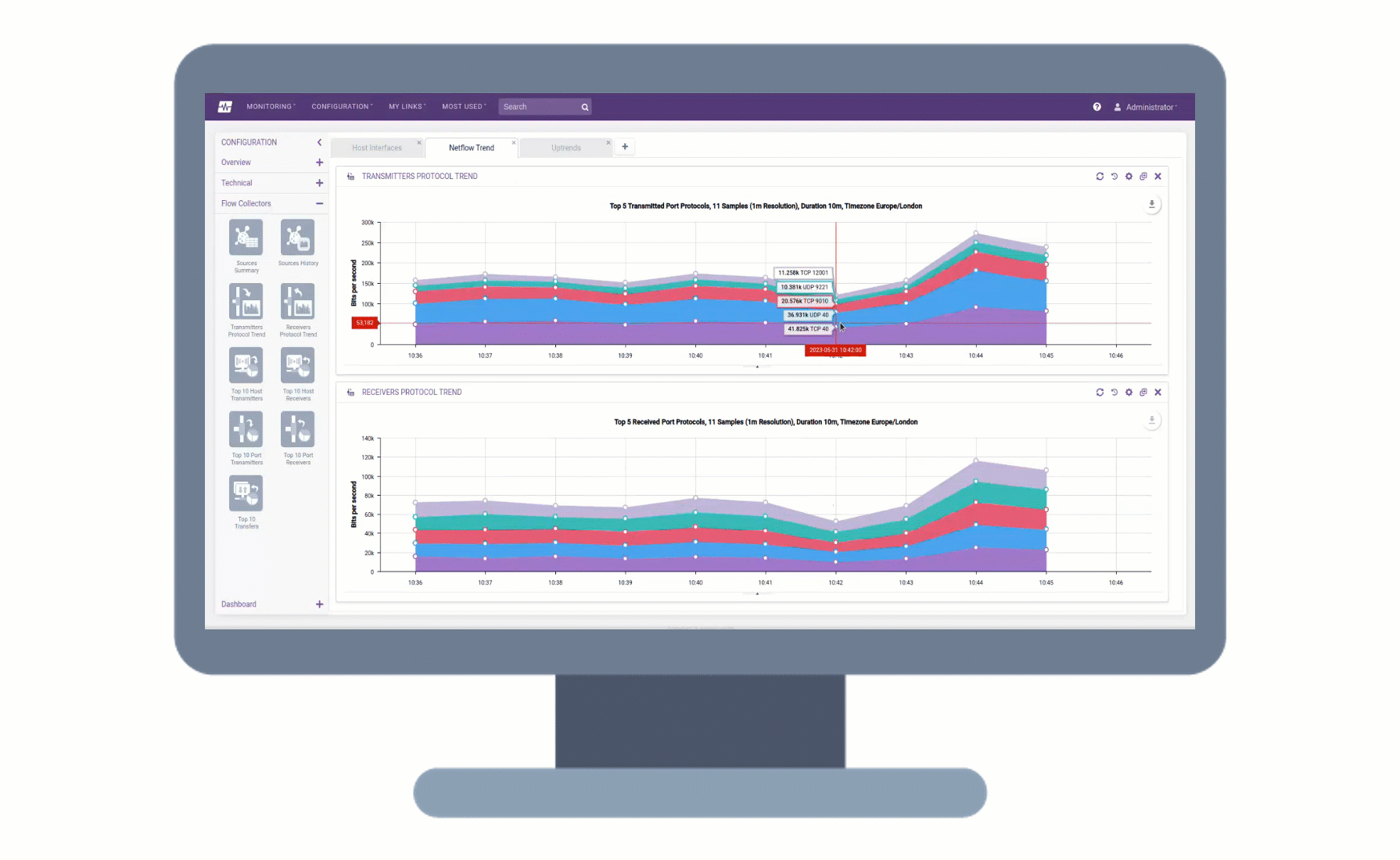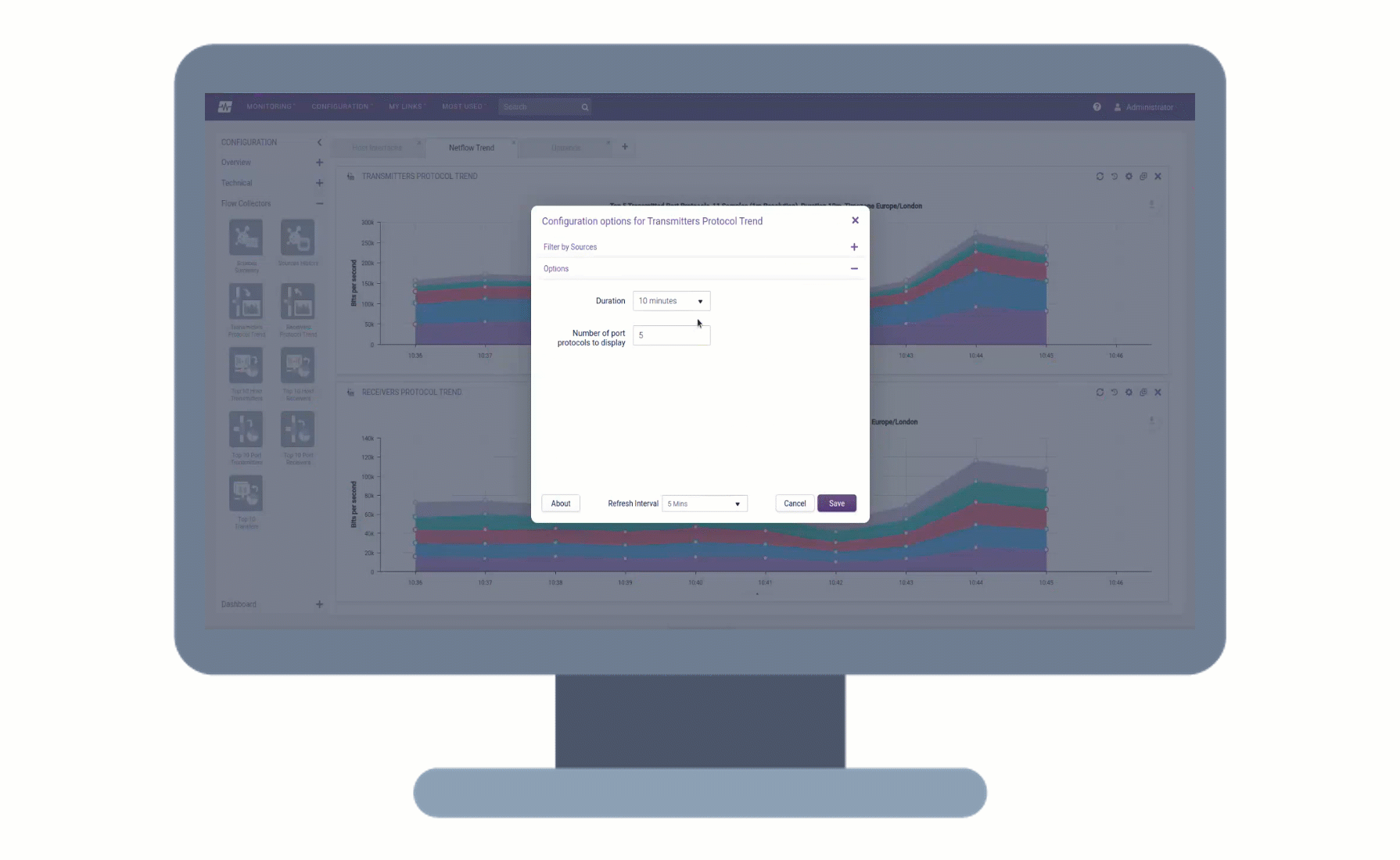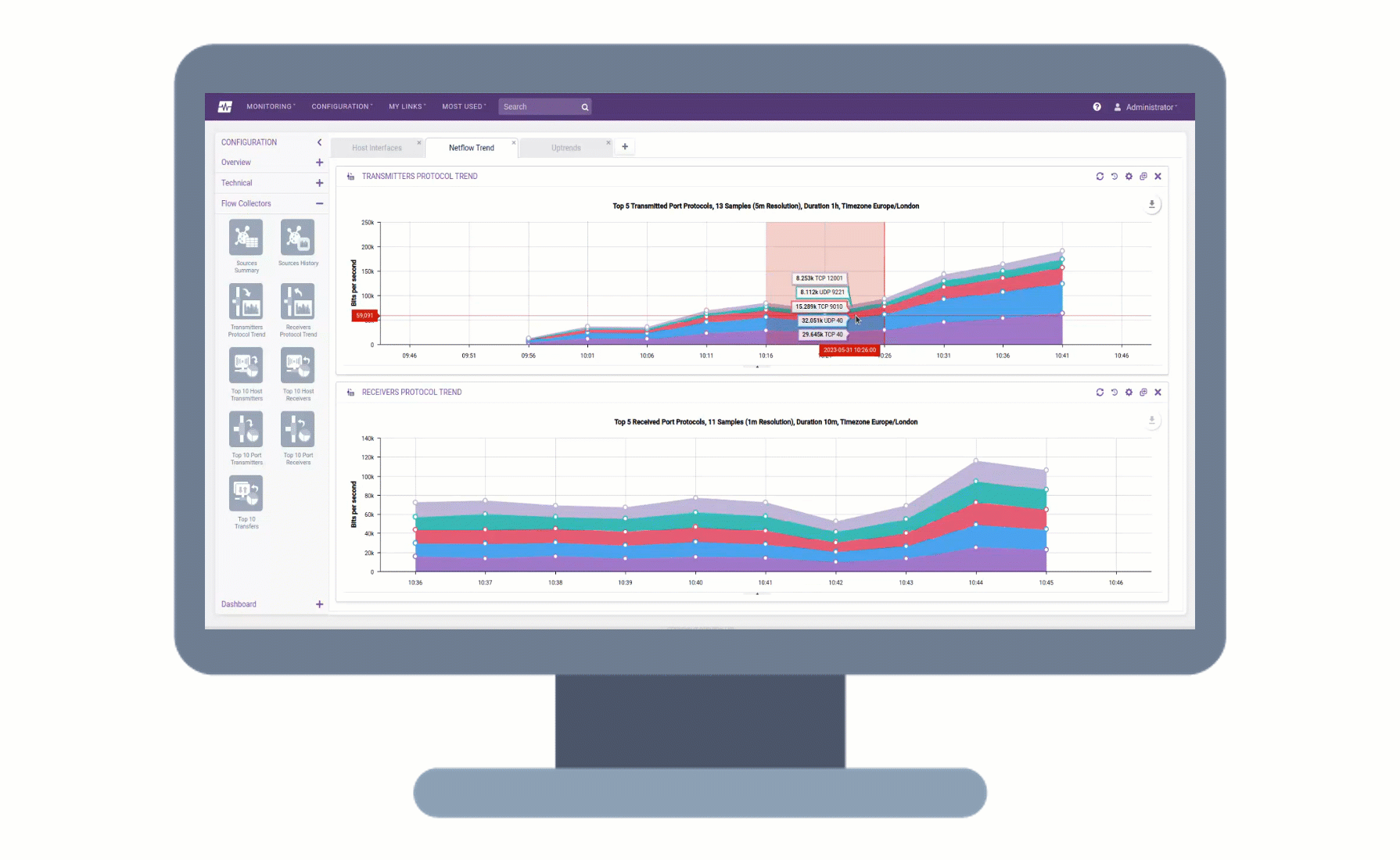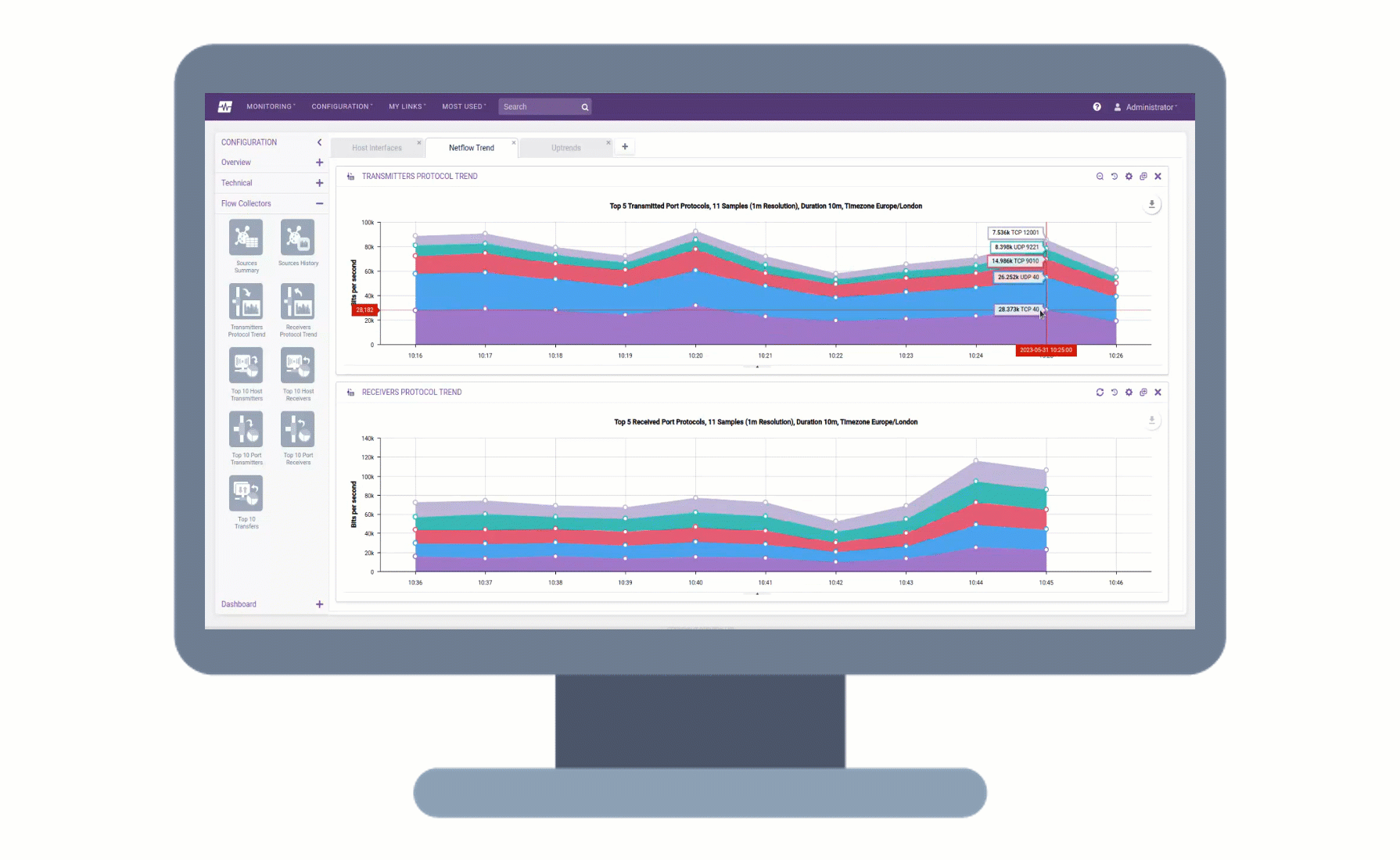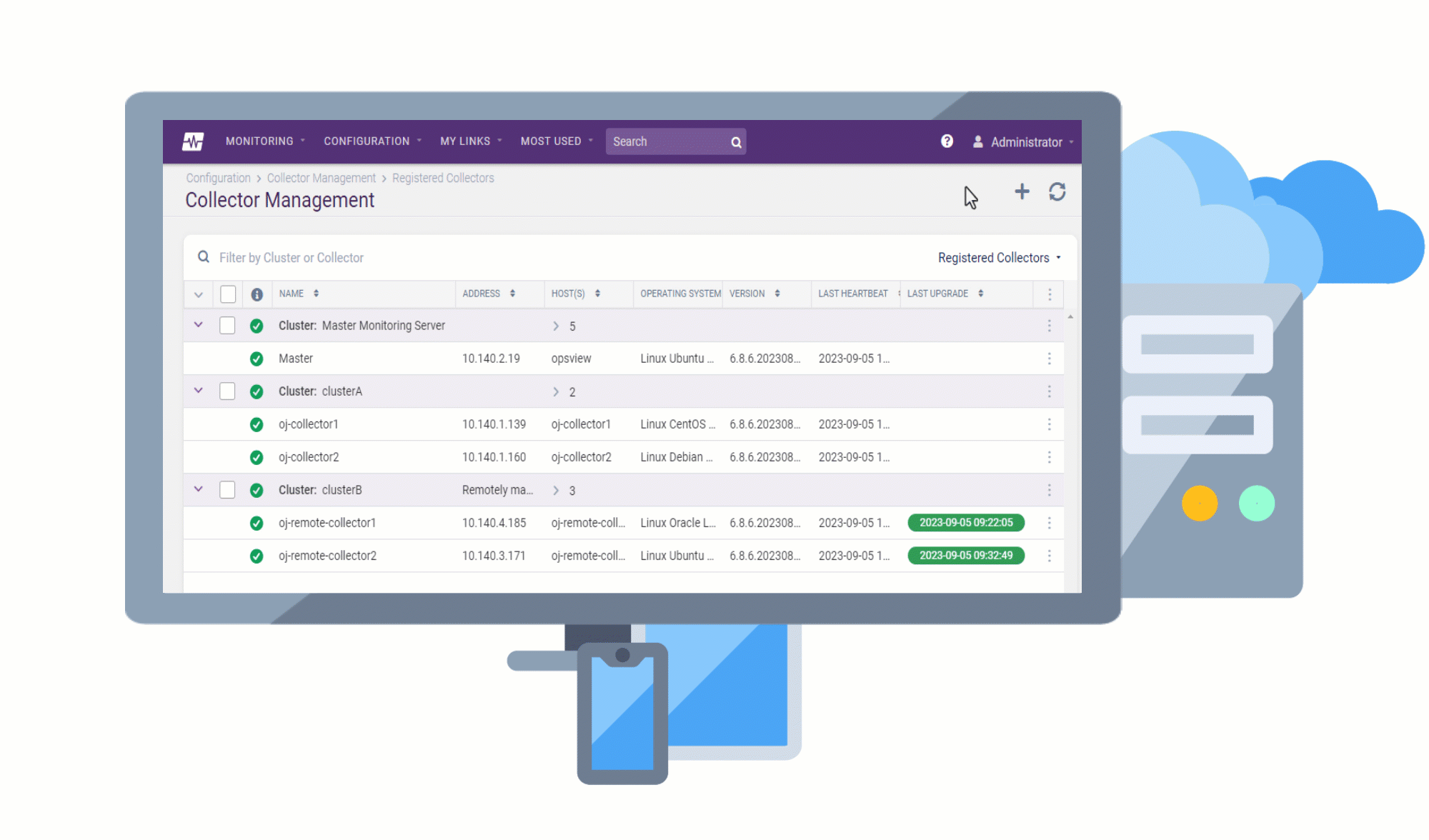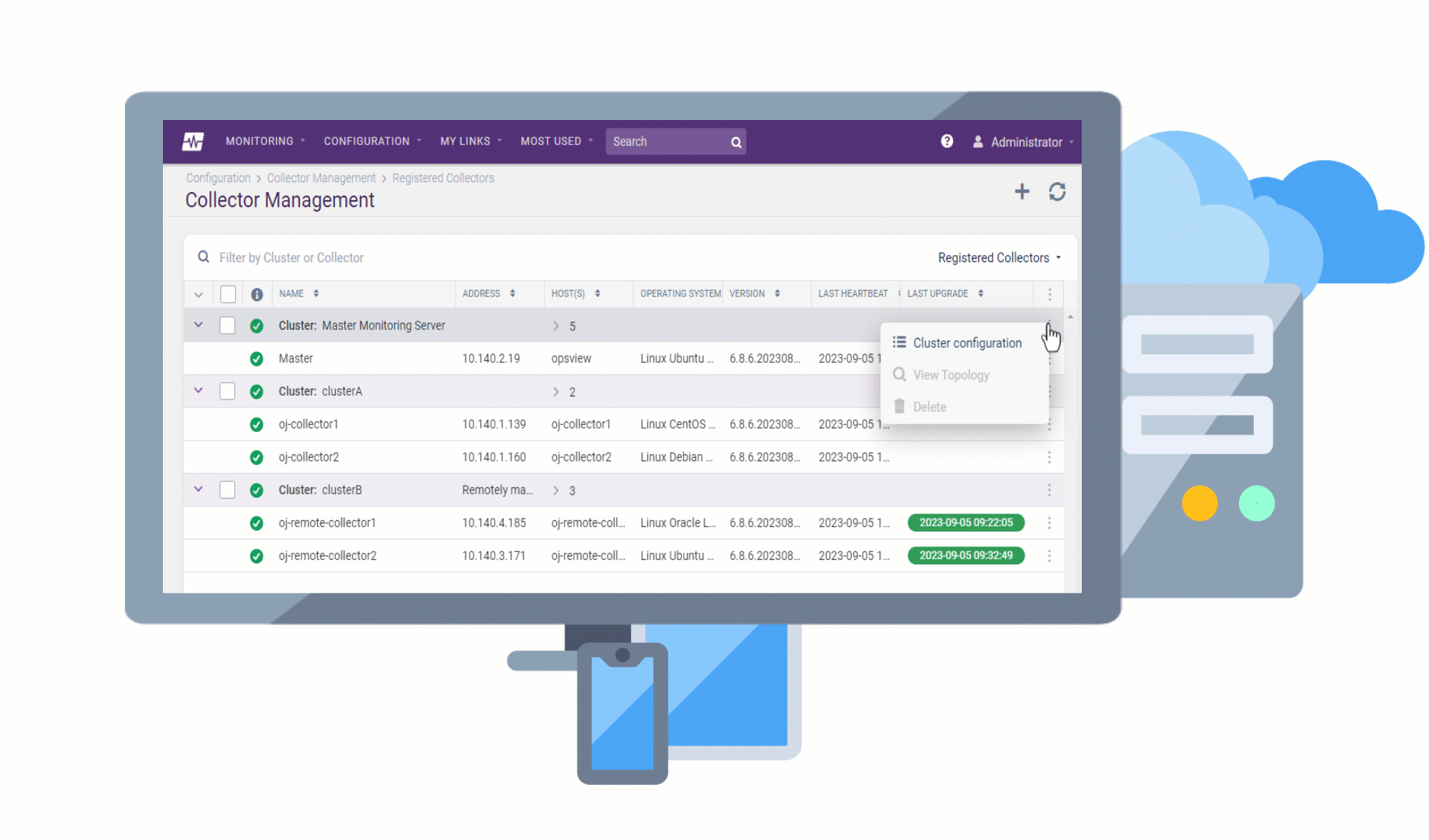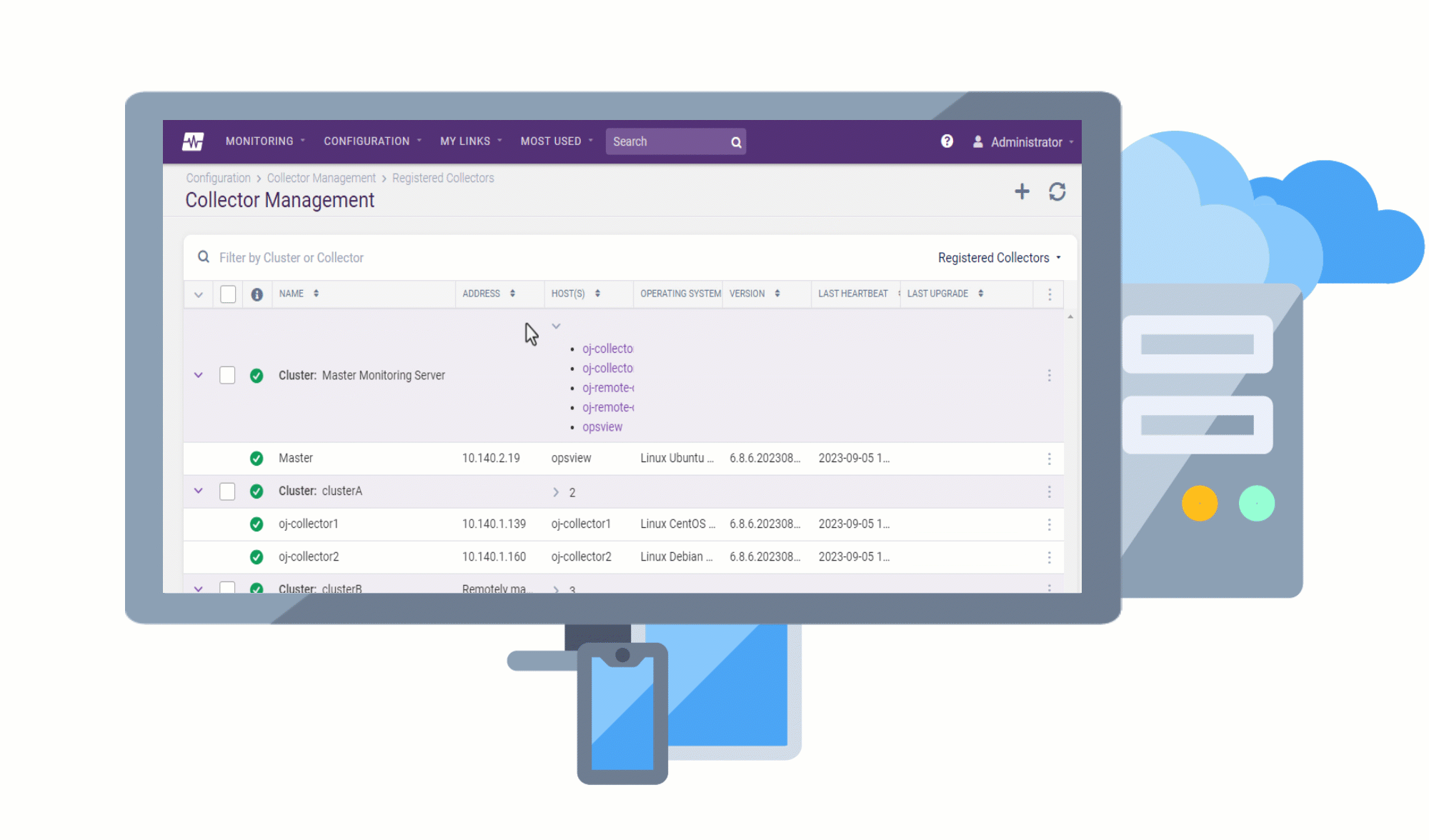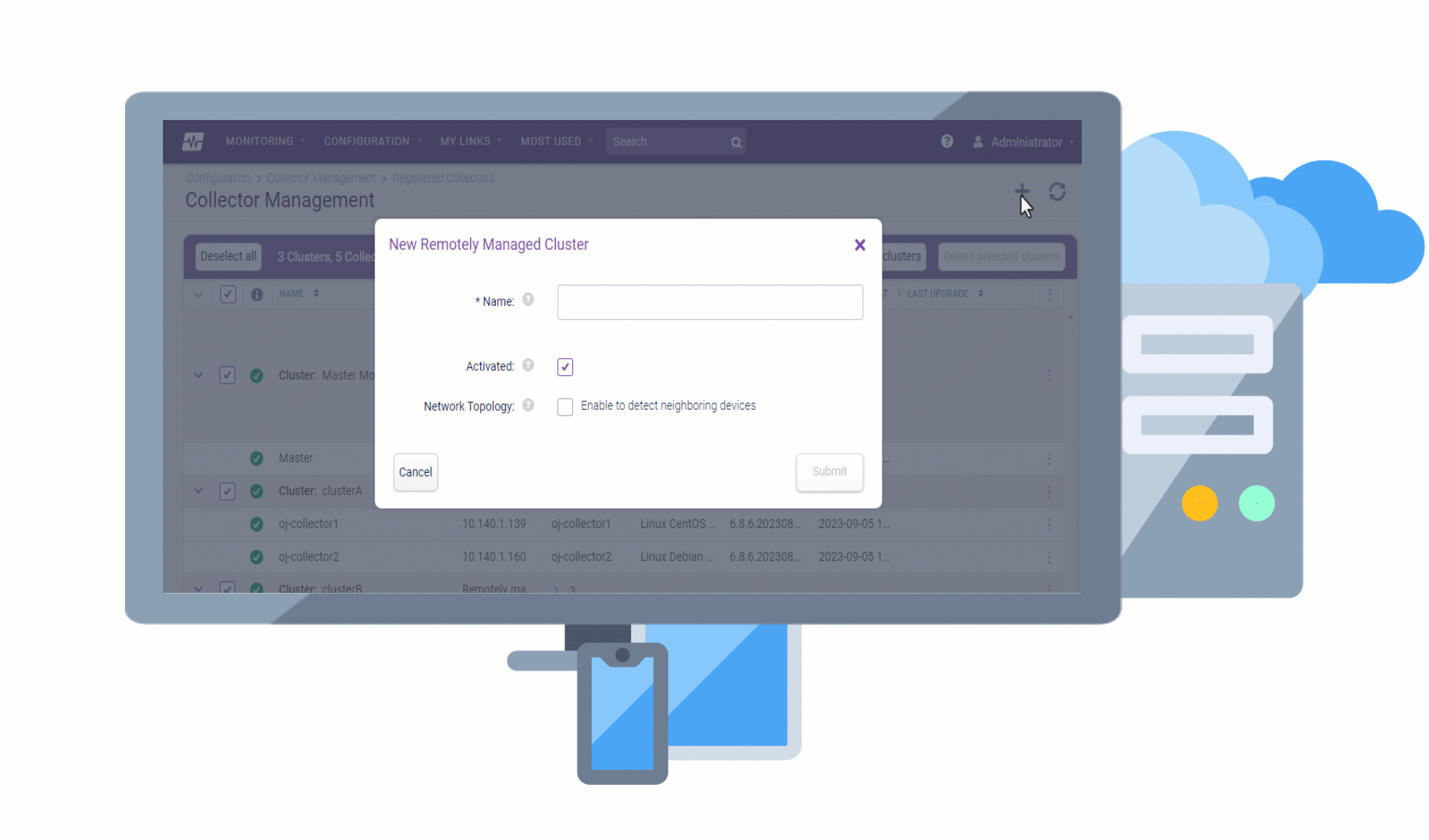
Remote Collectors can now be registered and upgraded to later versions directly from the user interface, without the need for command-line access. This makes the upgrade process more convenient and efficient, as you can track the progress of the upgrade in the UI and view any upgrade activities that are logged.
Replacing the Monitoring Collectors page, the Collector Management page has been revamped to ensure that all elements in the UI are aligned and styled consistently, making the page more visually appealing and easier to use.